NF Post 7 : Network Forensics Investigative Methodology (OSCAR)
Similar to other forensic task, discovering and analyzing evidence from network sources has to be done in steps so that the results can be accurate. Forensic investigators should perform our activities within a methodological framework. According to Sherri Davidoff and Jonathan Ham in Network Forensics : Tracking Hackers through Cyberspace, the recommended way to recover a digital evidence is:
- Obtain information
- Strategize
- Collect evidence
- Analyze
- Report
This steps is called OSCAR methodology. Here’s some brief description of each step.
1.Obtain information
Getting information related to the incident and gaining information about the environment when the incident occurs.
Knowing the following things are important:
• Description of what happened (as is currently known)
• Date, time, and method of incident discovery
• Persons involved
• Systems and data involved
• Actions taken since discovery
• Summary of internal discussions
• Incident manager and process
• Legal issues
• Time frame for investigation/recovery/resolution
• Goals
2.Strategize
Working efficiently and effectively is an important trait of an investigator. Communication is a must, so an investigator has to frequently communicate with other investigator regarding the case. Make sure everyone is working in concordance and that important developments are communicated. Prioritization of evidences is also needed. Here’s an example of evidence prioritization.
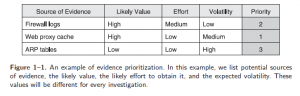
3.Collect evidence
The investigator came up with an acquisition plan based on the sources of evidence from the previous step. Then, based on the plan, collect evidences from each source. Here are 3 things an investigator must address in every evidence:
- Document -> Store the evidence securely, it may be referenced in court, and the notes might be helpful in the future
- Capture -> Capture each evidence
- Store/Transport -> Store the evidence securely and maintain the
chain of custody. Keep eyes on who can access the evidence.
4.Analyze
Usually, the analyzing process in nonlinear. But these following things should be essential:
• Correlation
• Timeline
• Events of Interest
• Corroboration
• Recovery of additional
• Interpretation
5.Report
The report that the investigator produce must be:
• Understandable by nontechnical laypeople, such as:
– Legal teams
– Managers
– Human Resources personnel
– Judges
– Juries
• Defensible in detail
• Factual
Reference:
Sherri Davidoff, Jonathan Ham – Network Forensics: Tracking Hackers through Cyberspace (2012, Prentice Hall)